Data security is a growing concern for many businesses, and with good reason. The recent high-profile data breaches have demonstrated that no company or individual is immune from cyberattacks. With more than 450,000 new malicious programs reported every day, it’s clear that protecting your business against such threats requires constant vigilance.
Whether you’re a small- or medium-sized business, large corporation, educational institute, or government agency, entities of all sizes are likely affected by the ever-evolving cybersecurity landscape. The threat levels are constantly changing and organizations must continually update their detection tools and processes in order to protect themselves from malicious attackers who are looking for gaps in existing defenses.
From physical access controls such as CCTV cameras, swipe cards, PIN codes, and biometric sensors to software-based solutions like antivirus programs, firewalls, and anti-malware, there are several ways modern technology can be used to improve information security within a business.
However, many security solutions focus on detecting known threats rather than preventing potential ones. Furthermore, most traditional approaches rely heavily upon human intervention, often leaving vulnerabilities open for hackers to exploit.
To effectively address risks posed by advanced persistent threats (APTs), web intrusions, targeted attacks, and other sophisticated attacks, your organization needs to implement technology that provides real-time protection against unknown threats while ensuring compliance with industry standards and regulations.
Read on to learn how to ensure you stay ahead of the curve and keep your company secure, even when you can’t be there every minute of the day.

What Is Being Security Conscious?
Security consciousness is being aware that your business could be attacked at any time and being prepared to defend against it.
It’s about staying vigilant and doing whatever it takes to keep yourself, your employees, and your customers safe. A security-conscious company is proactive and takes steps to minimize risk and vulnerability, including installing and updating security measures.
Why Should You Be Security Conscious?
As the risk of becoming a victim of a major digital attack grows, businesses of all sizes need to adopt a security-conscious mindset to avoid having their data exposed and their reputation damaged.
Many small businesses are already victims of cybercrime because they lack the resources to monitor and guard against online threats adequately. However, with the right amount of forethought and planning, any size company can protect their sensitive information.
When your current security tools and practices don’t protect your business, your company will become easy prey for those who seek to harm you. By taking on a security-conscious outlook, you can increase awareness of potential threats and take actions to mitigate them.
Measures To Make Your Business More Security Conscious
What Is Being Security Conscious?
The first step toward implementing an effective security program is knowing what threats exist and where they come from when they do. Once you have this knowledge, you can decide how to handle each type of threat.
The goal here is to reduce the likelihood or impact of a successful attack and help identify potential gaps that could allow malicious actors to infiltrate your premises and network undetected.
Threat intelligence has become more prevalent as organizations attempt to gather information on attackers before a breach occurs. With the many different methods available, choosing the most appropriate one for your business requires research and consideration.
Educate Your Employees
Once you’ve identified the risks and threats to your business, you should start educating your staff on how to spot these issues and take necessary precautions so you aren’t caught off-guard when an attempted breach occurs.
This includes training workers on how to recognize signs of a hack and how to respond appropriately. It’s essential to have everyone involved in the process. Not only do your employees play a key role in ensuring the safety of your systems, but they are also among the first to notice something amiss when someone tries to compromise your network.
Establish Security Policies
Next, you need to establish policies around security and privacy that outline specific procedures and guidelines every employee must follow. This helps prevent human error and ensures that every person involved in handling sensitive information understands precisely how to store it and to only share it with those with access rights.
Your policies should guide how everything from passwords to customer data should be handled; how data should be shared within the organization; how access control security is carried out, etc.
Incorporate Physical and Digital Security Controls
While security policy is essential, it’s just one part of the equation. You still need to put in place the proper access control model to ensure that your guidelines can be followed effectively.
That means installing physical security measures such as cameras, locks, alarms, etc., and digital security solutions like firewalls, intrusion detection/prevention systems, access control software, encryption software, and VPN services.
As threats continue to evolve, so must your company’s security posture. Unfortunately, it’s not always possible or practical for companies to devote their IT team full-time to computer security.
With Elliott Data Systems, you’ll receive expert advice about implementing a comprehensive security strategy from consultation to setup and training. We also provide ongoing support so you can keep making gradual improvements as needed. To learn more about how we can help you improve your cybersecurity, please call us at 1-888-345-8511.
It doesn’t matter what size your business is or where it operates; you can be more secure by implementing a layered defense strategy.
Here are several ways to boost your security:
Physical Access Control Solution
Businesses often overlook physical access controls as a critical part of their perimeter security. However, secure IDs, smart card readers, visitor managers, and video surveillance offer substantial advantages over traditional protection methods because they limit unauthorized persons from gaining entry into sensitive areas without notice.
If you don’t have appropriate access control policies, anyone who knows where your doors are located can access your office. Even if someone only wants to look around, this infiltration method makes it much easier for ill-intentioned intruders to get inside undetected.
Here are different measures you can take to make your business premises more secure:

Print Secure ID Cards
Print secure ID cards with sophisticated credentials that are hard to duplicate. These cards can feature unique tactile impression patterns, holograms, bar codes, QR codes, encoded magnetic stripes, and other advanced security features that authenticate an individual’s identity when presented to a reader.
Secure ID cards are most effective when used in conjunction with other physical security measures, making them excellent measures for high-risk facilities.
Replace Proximity With Smart Cards
In an access control system, the smart card is an advanced contactless access card that provides a higher level of authorization than proximity. It is designed to give you more flexibility in data storage and card use.
Along with access control, smart cards can be used for payments, network security, telecommunication, and much more. With smart cards, you can monitor employee activities, enforce rules, manage attendance, and perform other tasks. They also allow you to track employees remotely and set role-based access control and permissions.
Switch From Paper-Based to Electronic Visitor Management
An electronic visitor management system (VMS) eliminates the need for visitors to manually sign in and out, thus reducing human error and increasing efficiency. VMS technology allows you to limit access rights based on departments, time of day, or even individual visitors.
This system lets you know which individuals enter certain rooms and when. Using these metrics, you can quickly identify visitors who might be conducting nefarious activity and determine which ones should be denied or granted access.
Install Cloud-Based IP Surveillance System
A cloud-based IP camera solution combines the safety of your recordings with easy access anytime, anywhere. You can instantly review footage of any suspicious activity while ensuring complete privacy from outside parties.
You can detect fraud, record regulation compliance, identify potential security risks, locate people, track equipment, monitor employees, and conduct audits. An easy-to-use dashboard gives you instant alerts when something goes wrong.
With IP-based VMS, you can view live footage from anywhere within your organization with an authorized device. You can even use mobile applications to remotely check up on your property while you’re away.
Automate Vehicle Identification Systems
Vehicle access management is designed to manage the entry and exit of vehicles at corporate offices, universities, and other high-security areas like government and military environments.
They can be used as stand-alone systems or integrated with existing access control models. The integration of vehicle identification with access control systems provides an added layer of security by not only restricting access to authorized vehicles, but also to authorized drivers.
This helps an organization manage and monitor its fleet, as well as protect the perimeter.
Maintain Asset Tracking
Asset-tracking capabilities help keep businesses safe. The most common uses include asset inventory, inventory verification, and physical location. Using RFID, Bluetooth, or GPS technologies, this system can notify you if your assets are lost, stolen, or moved.
RFID tags have been a popular choice among the many asset-tracking solutions available today. These tags can be embedded into machinery, tools, handbooks, computer equipment, and more.
Digital Security Solution
Deterring criminals from entering your business premises is just one part of which security measures should be in place. Another equally important component is preventing information leaks and data breaches.
Many companies are vulnerable to cybercrimes, such as identity theft, malware infection, ransomware attack, and loss of confidential data.
With all these issues popping up, your network must have a robust digital security solution.
Here are some measures you can take to secure your business online:

Establish Password Policy
Passwords are often a weak point when securing your business online. Hackers can easily break into computer systems using stolen passwords and obtain valuable business data.
A firm password policy will prevent users from creating easy-to-crack passwords while helping ensure user accounts remain protected.
Use Two-Factor Authentication (2FA)
Two-factor authentication ensures that your account isn’t compromised even after someone obtains access to your email address or phone number.
Multi-factor authentication allows for additional layers of protection, providing extra security against potential threats.
For instance, requiring two forms of authorization from two devices may prove beneficial in mitigating the risk associated with fraudulent activity.
Install Firewall Protection
When hackers gain unauthorized access to your computer system, they can use this access to install malicious software on your company’s servers.
Software firewalls provide another layer of defense by ensuring that outbound traffic is appropriately filtered and restricted.
Utilize Cloud Backup
Having an offsite backup plan is crucial to protecting important documents and data. As technology evolves, so do hackers – they could gain access to and delete your company files on your network if given the chance.
A cloud-based backup system prevents data loss caused by hardware failure, natural disasters, hacking, or other unforeseen circumstances.
Implement Data Encryption
Encrypted file transfers between computers are the easiest way to protect confidential data. Data encryption ensures that only authorized people can read sensitive information stored on the network.
Encrypting file transfer protocols make sure your data remains private during transmission.
Ensure Safe Login
Enabling login verification keeps hackers from logging onto corporate networks without proper authorization. It also helps reduce the likelihood of employees unintentionally sharing personal credentials.
To make sure your company’s IT infrastructure is running smoothly, schedule regular maintenance checks.
Restrict Access
One of the best ways to keep bad actors out of your business is by restricting their access to company resources. Mandatory access control solutions allow administrators to establish user privileges, preventing them from accessing certain areas of the network.
Manage IT Services
Your IT team should be knowledgeable about the latest technologies and how to implement them. A managed service provider can make updates and patches and monitor and maintain your security solutions.
These services help ensure your network stays up-to-date with current attack strategies and protects your company from cybercriminals.
Security Awareness Training
The success of your cybersecurity and physical threats strategy relies heavily on employee involvement. Employees who have been trained on topics such as secure communications, data privacy, and essential network management can help mitigate risks.
This training provides a foundation for the rest of the cybersecurity program. The more familiar your employees become with these concepts, the less likely it is they will make mistakes when faced with unfamiliar situations.
By creating this security culture, businesses become less vulnerable to cyberattacks.
Perform Regular Audits
Auditing company systems regularly will uncover potential vulnerabilities before they become problems. Network scans, penetration tests, web vulnerability assessments, and malware analysis are some examples of standard audit tools used to check for weaknesses. These audits help identify areas where you can improve your infrastructure’s overall security posture.
Regularly performing these types of audits will give you insight into what is working and what needs improvement. You’ll know which steps must be taken immediately to fix issues before they become more significant problems. The bottom line is if you don’t look at your systems often enough, you won’t discover any potential problems until it’s too late.
Get Peace Of Mind With Elliott Data Systems
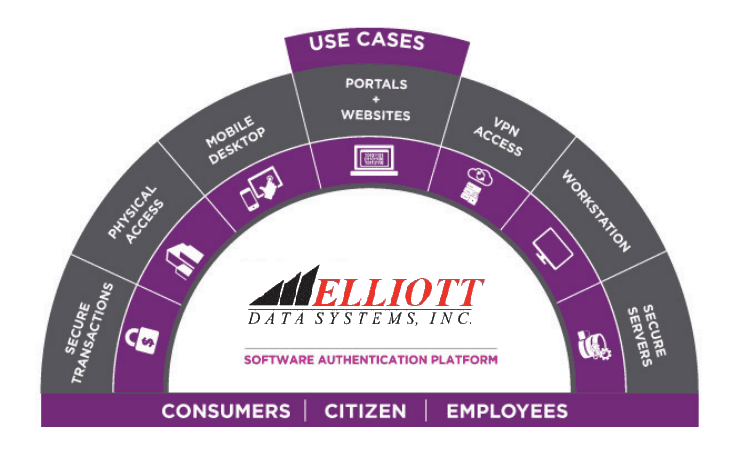
Elliott Data Systems has implemented an array of security features to help businesses stay safe from intruders inside or outside their network.
From secure logical access protection solutions to attribute-based access control systems, we offer comprehensive solutions to provide peace of mind 24/7/365.
As an industry leader, Elliott Data Systems can support your business with everything from routine maintenance to user training for best utilization of your integrated security systems. Our goal is to create a seamless, stress-free environment for your business or establishment by providing tailored security solutions that fit your unique requirements.
Contact us today or call us at 1-888-345-8511 to learn more about how you can make your business safer than ever.

