Two Factor Authentication Overview
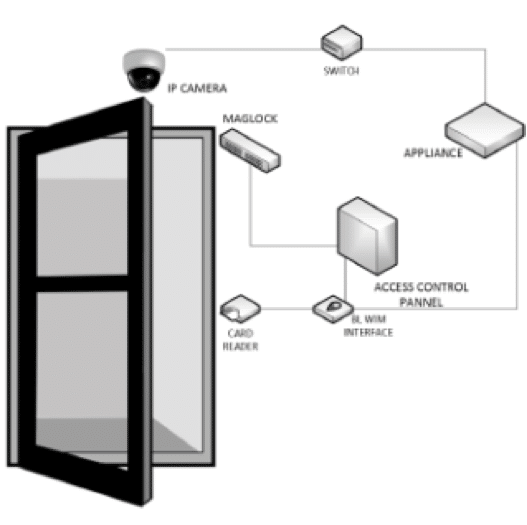
Access control systems control doors and locations. To prevent misuse, access control provides a way to monitor, control, and manage a door’s “status.” The access control software can allow or deny a user of the token, and is based on door location, designated timeframe, and authorization privileges.
The inherent security risk in single token presentations is theft, loss, being loaned to another user, or the token cloned to gain access. Facial recognition as a biometric two factor authentication assures the token matches the face and creates a much more secure environment.
Two factor authenticators are classified as:
- something you know (Password)
- something you have (Card, fob, cryptographic key)
- and something you are (Face, fingerprint, iris scans).
Blue Line Technology’s First Line Facial Recognition system with 2FA was designed with the goal of creating a safer and more secure environment, allowing multiple client locations to work seamlessly.
 Using a 1:1 matching process, First Line Facial Recognition Software provides an extremely accurate validation process for 2FA authentication, threat detection, and an enterprise approach to better protecting employees, visitors, and customers.
Using a 1:1 matching process, First Line Facial Recognition Software provides an extremely accurate validation process for 2FA authentication, threat detection, and an enterprise approach to better protecting employees, visitors, and customers.
This solution requires a token (card/FOB/code) and a registered face to gain entry. Our software matches your current token to your face. Once the token is presented the software (via camera) immediately verifies the person using the token is the authorized user. The 2 factor authentication occurs at the speed of the token with no delays for a face match process. If the face doesn’t match the card, entry is denied. With the Blue Line Technology API (Application Programming Interface), a biometric mismatch alert can also be sent to designated recipient. The Blue Line software is compatible with current access control systems eliminating the need for costly tear outs. The logic and reporting are performed by the existing access control platform with an added layer of performance. Alert messaging of threats can be sent via VMS/email/text to designated personnel.



