Secure interior and exterior doors using a variety of integrated access control software and locks. Assign full or limited access to access control doors by assigning rights to employee, student or visitor ID cards and adjust permissions at any time without reprinting ID cards.
Showing all 8 results
-

LoxIQ Cloud Access Control Management
Product DetailsLoxIQ® is a revolutionary phone-based software product delivered on Proxess’ wireless locking hardware platform. LoxIQ™ is designed to be understood by everyone with little training required…simple yet loaded with features.
-
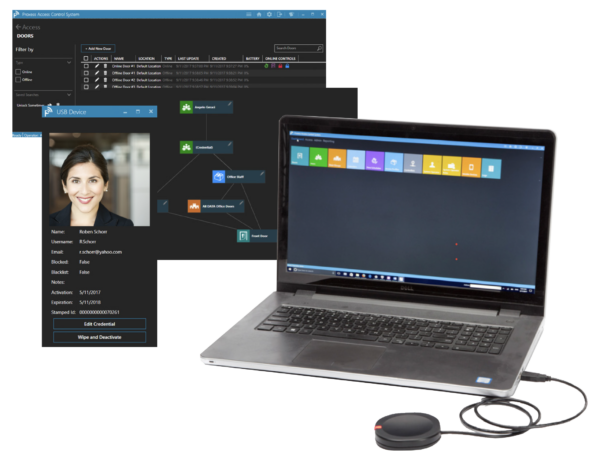
ProxessIQ
Product DetailsScalable Access Control Software
ProxessIQ™ is the scalable access control software supporting Proxess intelligent wireless locksets and door controllers. A ProxessIQ™ system can begin with a single wire-free lockset and incrementally expand to an unlimited number of locations, doors and users.
-

Bioconnect Link
Product DetailsBioConnect is unifying physical and digital access with the Link Solution. A convenient, flexible and scalable solution to add an additional layer of security to physical access points with two factor mobile authentication.
-

BadgePass One Access Control
Product DetailsTake your system to the next level with secure door access control in BadgePass ONE. BadgePass ONE access control allows for streamlined reader deployment and easy to manage door access privileges unlike any other door access system on the market. Coupled with a variety of user-friendly hardware options to choose from and a flexible subscription pricing model, access control has never been easier to deploy!
-
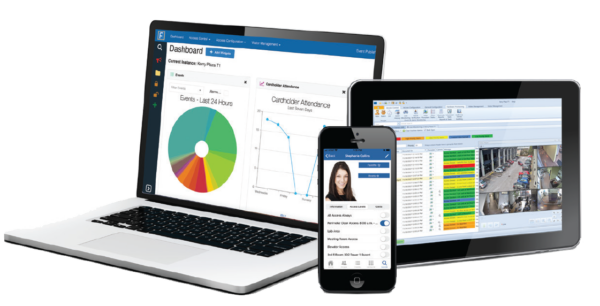
Feenics Cloud-based Access Control
Product DetailsFeenics is the industry’s most secure and flexible cloud-based access control solution that can be accessed anywhere using a simple user interface. Built on open architecture hardware and fortified by the security, disaster recovery, and redundancy of Amazon Web Services, Feenics is scalable from one door to global enterprise environments. It provides the ultimate choice to manage security infrastructures, integrate third-party applications and reduce capital expenditure.
-
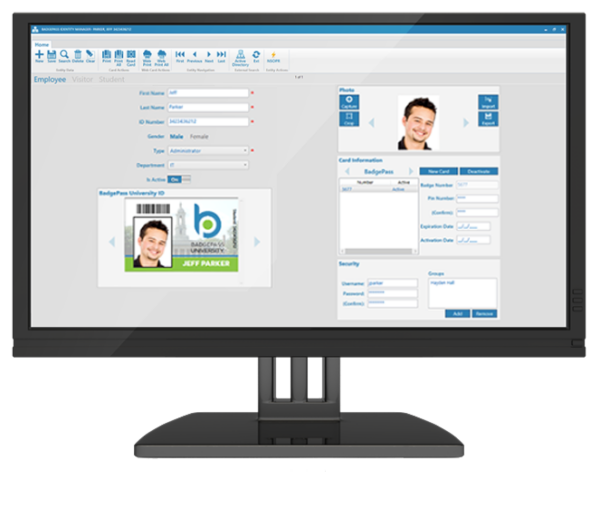
Access Manager Software
Product DetailsBadgePass Access Manager offers customers a new perspective on electronic door access. Built by ID industry experts who understand the importance of streamlined card issuance and activation, this user-friendly software allows customers to not only manage door access privileges with ease, but also increase security through our automatic badge activation process. BadgePass Access Manager is more than just door access control – it is a part of our complete credential management system, allowing you to do more with your badge!
-

Two Factor Authentication
Product DetailsTwo Factor Authentication (2FA) is becoming a powerful prevention protocol for thwarting unauthorized access, fraud, and cyberattacks. The physical security world is driving to protect sensitive information, and control staff and the public from accessing restricted areas. There is an increasing need to verify and authenticate user identity.
As security becomes more technologically advanced, so do the analytics behind addressing security needs. Two factor methods have become vital to the access control process, and will not only have to address the security concerns of the end user, they will also have to be flexible to the client’s network and current infrastructure. This white paper will explain the details of how the Blue Line Technology two-factor method works, and the practical use case scenarios that would benefit the client.
-

First Line Facial Recognition Software
Product DetailsFirst Line Software is an intelligent facial recognition, security software that provides automatic, real-time, identification verification for threat detection, access control, and concierge applications.


